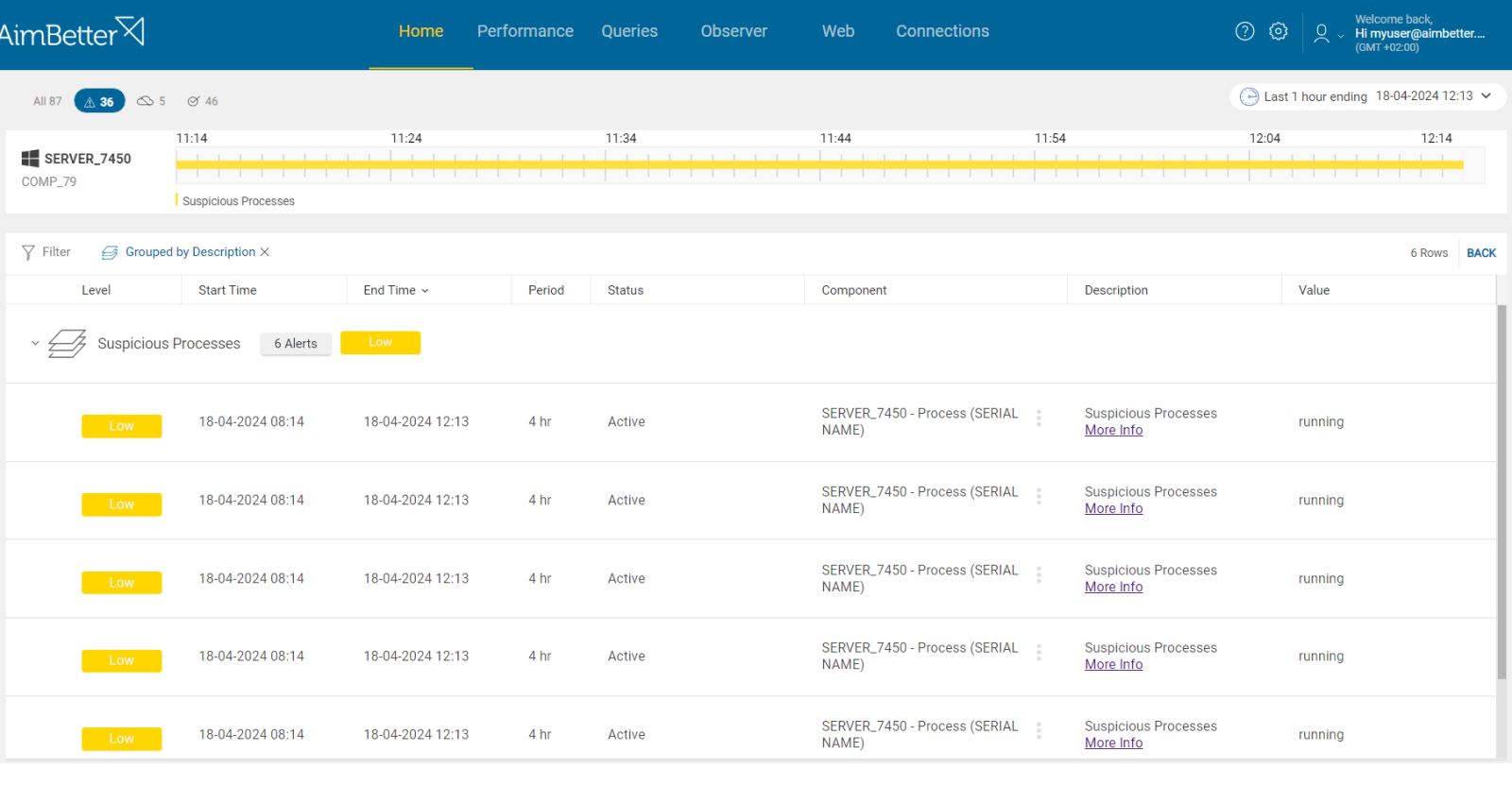
Multiple applications run on a company’s server to support business operations. On Windows OS, each running application is represented by a process. To monitor specific applications that may impose some risk on the company, AimBetter provides the ability to define “suspicious processes” for which an alert is triggered.
Numerous processes can present a risk to the company and vary depending on the nature of the business, its infrastructure, and the specific security policies in place. However, some common types of processes that might pose risks include:
Malicious Software: Processes associated with malware, such as viruses, worms, or ransomware, can infect systems, compromise data integrity, and disrupt operations.
Data Leakage: Processes that handle sensitive information without adequate security controls may inadvertently expose data to unauthorized parties, leading to breaches and compliance violations.
Resource Exhaustion: Processes that consume excessive system resources (e.g., CPU, memory, disk I/O) can degrade performance, cause downtime, or even lead to denial-of-service (DoS) attacks.
Insecure Communication: Processes that transmit data over insecure channels or protocols may be susceptible to interception, eavesdropping, or man-in-the-middle attacks.
Backdoors and Trojans are processes designed to provide unauthorized access to systems or execute malicious commands. Attackers often install them to maintain persistence and control over compromised systems.
Data Breach Response Processes: While not inherently risky, processes related to incident response or data breach management may indicate that a security incident has occurred, highlighting potential vulnerabilities or weaknesses in the company’s defenses.
Impact:
Programs remaining open unnecessarily might cause slowness because they consume the server’s resources. In addition, possible attackers might have breached your system and installed malicious programs to steal information or cause damage.
Expected behavior
By monitoring and managing these processes effectively, organizations can mitigate risks and strengthen their overall security posture.
1- Suspicious Process Activity.
Some processes, defined as suspicious due to the risk they may impose on the company, are running on the server’s company.
Problem identification:
Identify the suspicious program process running on the server and verify its approval and awareness.
The process activity will be displayed in the Windows Task Manager under the Processes Tab. You can enter it at any moment but you cannot know when the suspicious process may be running to catch it.
There is no need for manual tracking once any suspicious process activity on the server is notified, including the user name.
Recommended action :
Implement robust access controls, deploy security solutions like firewalls and antivirus software, conduct regular vulnerability assessments, and educate employees about security best practices.