Secure-by-Design
Our architecture ensures the highest level of security based on the following core principles:
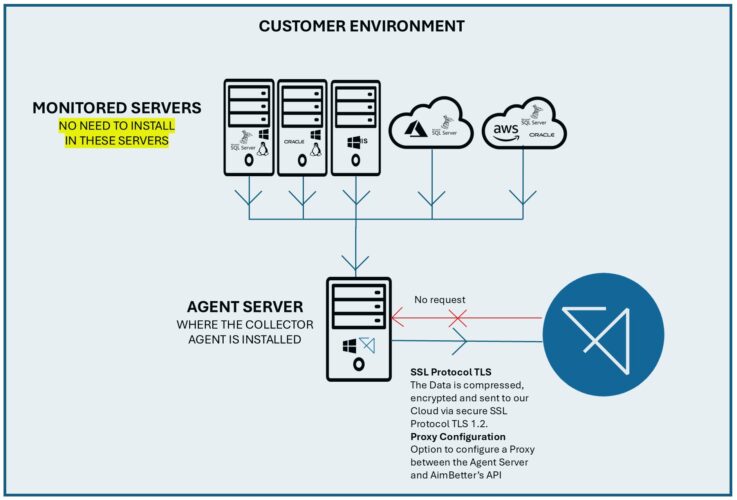
1️⃣ Single Collector Agent with Minimal Permissions
- Installed in the customer’s network
- Operates with least privilege to minimize security risks
- Ensures no direct access to database content
2️⃣ Secure Encrypted Transmission
- All data is encrypted in transit and at rest
- Prevents unauthorized access and interception
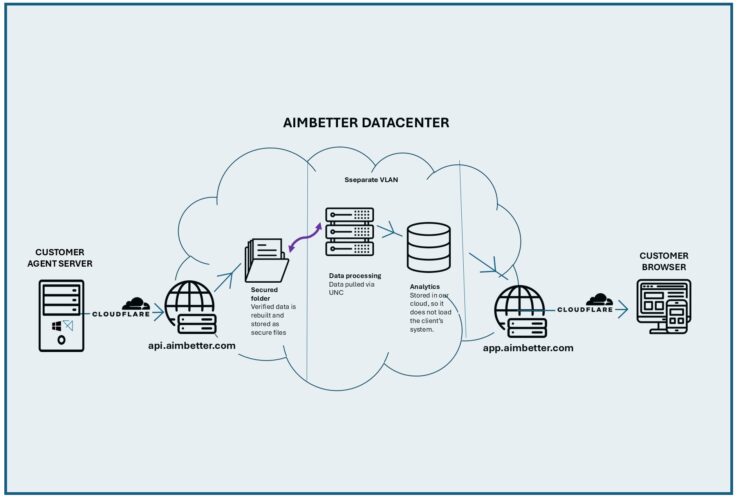
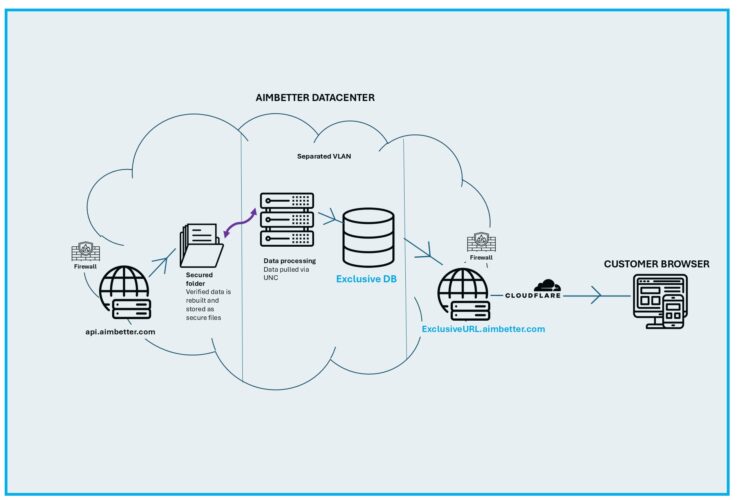
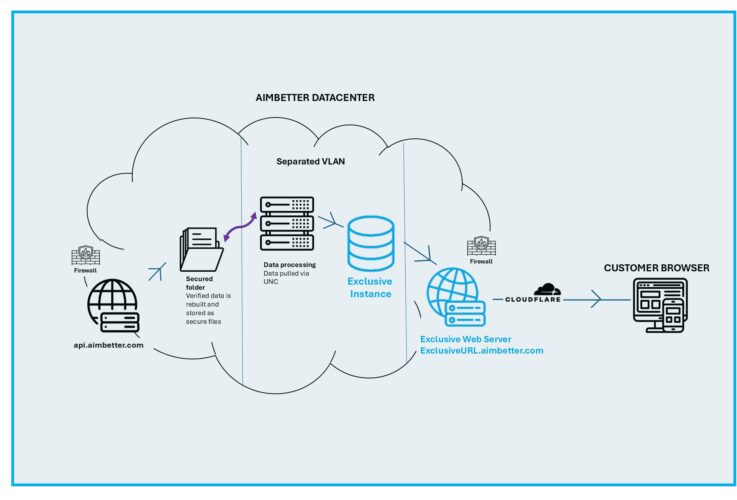
3️⃣ Highest Security Standards in a Multi-Tenant* Datacenter
- Complies with leading security frameworks and regulations
- Provides data isolation between tenants using a set of secure protocols
*For customers with more stringent compliance requirements, we offer premium security options
4️⃣ Secure Access to Web Application
- Enforced security controls, including login failure limits, session protection, and IP-based access restrictions
- Support for enhanced authentication methods, including 2FA and SSO
What Data Does AimBetter Collect?
- Windows Servers:
Real-time data on running processes, CPU and memory usage, disk performance, network activity, services, time settings, and system events, based on WMI. - Linux Systems:
Gathers OS version, active processes, CPU and memory stats, I/O performance, disk and swap usage, network traffic, and service status through standard system commands. - Microsoft SQL Server:
Collects query execution statistics, wait times, session and transaction activity, index and storage usage, high availability status, and system configuration using DMVs and system views. - Oracle Databases:
Extracts performance data, including SQL performance, session tracking, job scheduling, storage, configuration, and critical alert logs from V$ views and DBA tables.
You can check all the data sources in the Agent Viewing List.
These premium security conditions incur additional infrastructure and maintenance costs and require an on-demand quotation based on the customer’s specific needs.
Secure-by-design additional references
As part of AimBetter’s Zero Trust policy, our agent access is restricted to the Data…
ISO 27001
We are proud to announce that AimBetter has completed the ISO 27001 Compliance process. ISO…
How AimBetter helps you achieve GDPR Compliance and Peace Of Mind
Meaning of General Data Protection Regulation General Data Protection Regulation (GDPR) applies rules that companies…