What is a Cyber Ransom Attack?
A cyber ransom attack, also known as a ransomware attack, is a type of malicious cyberattack where hackers infiltrate a computer system or network, encrypt valuable data, and demand a ransom in exchange for decrypting the data and restoring access to the victim. The ransom is typically demanded in cryptocurrency to make it harder to trace. Ransomware attacks can cause significant disruption to businesses, organizations, and individuals, often resulting in financial losses, data breaches, and operational downtime.
How do Hackers Infiltrate a Computer System or Network?
Hackers infiltrate through malware via various methods. They may deliver malware through email attachments, malicious links, compromised websites, or infected USB drives. Exploiting vulnerabilities in software, operating systems, or network protocols is another common approach. Additionally, they use social engineering tactics to trick users into downloading and executing malware. This could involve impersonating trusted entities or creating urgency or fear.
Malware, short for malicious software, encompasses a wide range of harmful programs designed to disrupt, damage, or gain unauthorized access to computer systems or networks. Examples include viruses, worms, Trojans, ransomware, and spyware. Malware can also be distributed through drive-by downloads on legitimate websites or disguised as legitimate software.
Once executed, malware can perform a range of malicious activities, such as stealing data, gaining unauthorized access, or damaging systems. Users can mitigate the risk of malware infections by regularly updating software, using antivirus programs, and being cautious of suspicious links and attachments.
Ransomware Attack Protection by AimBetter
Security protection against ransomware attacks and other cyber security breaches is available through the Aimbetter File Connection feature.
This is how it works:
A set of files are configured to be permanently monitored and analyzed 24/7, ensuring constant vigilance. Should any alteration occur within these files, AimBetter promptly sends an email notification to the company’s designated recipients. Additionally, within 60 seconds of detecting the change, a phone call alert is initiated to ensure immediate attention.
These monitored files can be configured as “canary” files. Canary files, along with files stored in canary shares, are deliberately selected to mimic desirable targets for ransomware infections but hold no critical value to the organization’s operations. They serve as early warning indicators, swiftly highlighting any potential ransomware activity without risking significant data loss or disruption to essential operations.
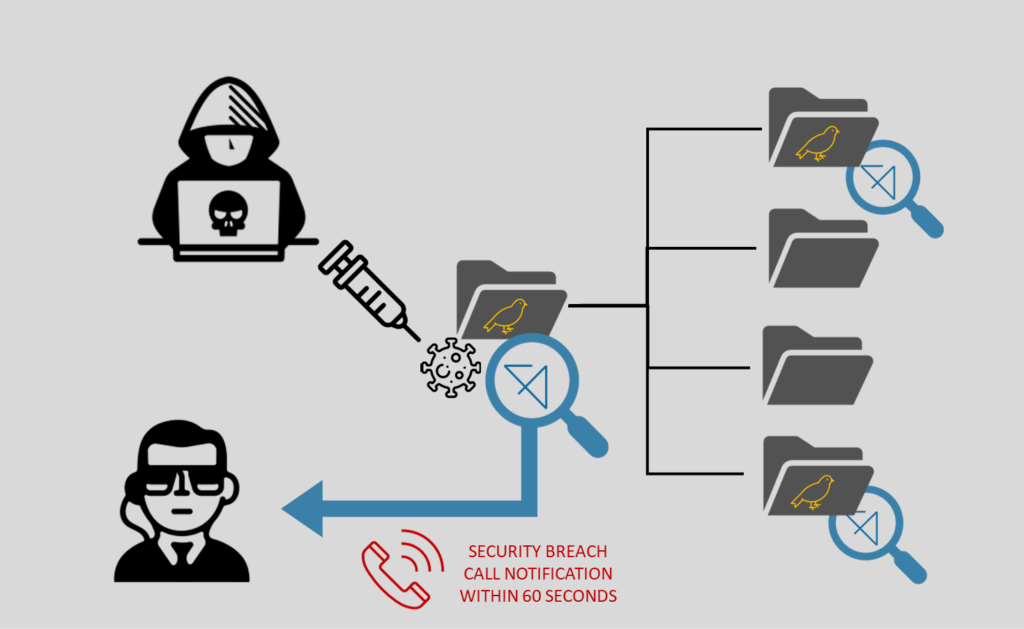
AimBetter customers can have this protection as an add-on for their comprehensive RTPS: Real-Time Problems Solving platform for as low as $1 dollar per file – for a minimum of 50 files configured.
For any questions, please contact us at [email protected].